What Are the Components of Access Control, and How Do They Work? Access control requires careful planning, whether you are using a single, central, or multi-site system. You must consider the changes in the environment, devices, inherent risks, and the growing movement to the cloud.
Terminal servers
In addition to Terminal Servers’ physical security, they are access control systems components, and a network firewall should protect them from unauthorized access. Microsoft added a step to modify the Default Domain Controller Group Policy Object (GPO) on the server. The license for Terminal Server is different than other applications. Microsoft grants a grace period of 120 days for setting up the licensing server.
In addition to allowing users to create session bookmarks, you can also configure a policy to prevent rewriting URLs that point to a Terminal Services resource. You can do this by navigating the terminal services resource profile and clicking the Bookmark link. Alternatively, you can click the New Bookmark link on the user role page. Once you have set up the resource profile, you can create session bookmarks.
Readers
Readers are the most visible components of an access control system. They read the access card and transmit it to the control panel. They may also require the card to be inserted or swiped. Readers are generally mounted on doors, and the number of readers necessary will depend on how many entries are in the building. Some readers are semi-intelligent, while others are not. If the reader isn’t reliable, the control panel can be upgraded without interrupting normal operations.
The most common credential carrier is an access control card or key-fob. These devices contain a microprocessor and an aerial that activates when they come within a few millimeters of a compatible card reader. A card reader may also have a built-in keypad. This allows for two-factor authentication, where the cardholder must enter both the credential and the pin code to gain access.
Master station
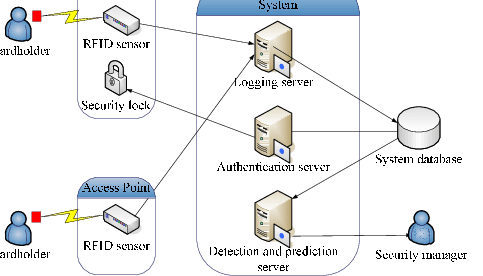
A building access system comprises four essential components: the Master station, an entry control unit, and a user input device. The master station interfaces with the entry control unit and the site controller and transfers updated access codes, schedules, and BAS-specific instructions between the two. It also provides centralized management of the entire system. This article explores the advantages of using a Master Station to manage an access control system. In addition, this article discusses the differences between access control systems.
A Master Station may contain multiple Sub-Stations. Each Sub-Station may be equipped with a station selector switch and an indicator light that indicates which station the visitor should be directed to. The Master Station may also feature a call button. When a visitor presses the call button, the Master Station will ring, and the associated indicator light will illuminate. Once the caller has been appropriately identified, the receptionist can press the station selector switch, begin the conversation, and the visitor will be guided to the next step.
Keypads
Access control systems include a keypad and an intelligent reader. An astute reader is a computerized device that detects a person’s identity and passes the information to a controller or panel. This controller/panel stores the transactional data and allows the door to unlock. Keypads are similar to readers in function. They receive input from authorized users and will enable them to open the door by entering the proper sequence.
Many keypad systems only provide access to registered tenants or staff members. Some tenants, however, need to provide access to guests. In such cases, the most effective system for controlling visitor access is a virtual key system. Virtual keys are unique codes sent to visitors before they arrive. The visitors simply enter these codes to gain access. Alternatively, you can use an access control system that uses a physical key. These systems are a convenient way to control visitors and tenants.
Servers
Authentication and authorization are essential components of an access control system. Both processes establish an individual’s identity and allow them to access a particular resource. Without authentication, access control will only protect the individual’s identity and not the data. Authorization determines what users are allowed to access. Authentication ensures that credentials are legitimate and are linked to a specific user account. When a user accesses a resource, the system will check if the credentials match the server database.
Another critical component of an access control system is an authentication server. These servers validate the credentials of clients. They can be either physical servers or dial-in user services. Most network access control solutions validate credentials based on named entities. More advanced solutions apply context-based or behavioral authentication. In either case, the server will be hosted in a public cloud. In addition to the authentication server, the access control system will also include a management console that allows administrators to control which users can access the network.
Software
In the beginning, you will need a server to store and manage the data of the access control system. The server will keep the list of approved users, called the allowlist, and it can be updated as needed. It will also record every entry and exit at the facility. The next step in the system is a user interface that controls which devices can enter and leave the facility. A web browser that supports this software will be essential.
Authorization is the set of actions that individual identity is permitted to perform. Authorization is a user’s right to access specific programs or files on a computer. Typically, this takes the form of reading, writing, and execution permissions tied to a username. These three elements work together to provide protection and cannot be bypassed. Identification and authentication help track user behavior—authorization limits access to certain functions, such as modifying security attributes or installing updates.
 Blog For Noob Random thought of a Noob Blogger
Blog For Noob Random thought of a Noob Blogger